Blog Post
Quantified Cyber Risk Through an ERM Lens in NIST IR 8286 Rev. 1
January 27, 2026
TL;DR
- NIST IR 8286 Rev. 1 clarifies how cyber risk should function within enterprise risk management, emphasizing integration, comparability, and decision relevance.
- Cyber risk is positioned alongside financial, operational, and legal risks, with senior leadership responsible for evaluating exposure.
- Cyber risk registers are reinforced as the primary mechanism for translating technical conditions into scenarios, impacts, and likelihoods suitable for evaluation.
- Aggregation and normalization are treated as essential steps for enabling cyber risk to move upward without losing meaning and to be compared across the enterprise.
- Cyber risk quantification (CRQ) is presented as a practical input to enterprise decisions, supported by business impact analysis, expert judgment, and calibrated data.
- A portfolio view of cyber risk enables leadership to assess trade-offs, allocate resources, and align risk decisions with organizational objectives.
Positioning Cyber Risk Within Enterprise Risk Management
Lack of data has rarely been a challenge that cybersecurity leaders in the enterprise setting have faced. In fact, cyber risk data is usually in abundance. The obstacle, thus, is instead twofold. Teams must first make sense of all of that information, and leadership must then be able to communicate what it means in a language that supports high-level decision-making. That gap between information and deeper understanding is where many cyber risk programs flounder.
Technical details often accumulate faster than they can be translated into a proper business context. Metrics, dashboards, and reports may be accurate and demonstrate progress in terms of risk mitigation, but they will still fail to inform critical decisions related to funding or risk acceptance. In short, the issue is neither visibility nor knowledge-sharing. Everyone has access to the data. The problem is being able to interpret this data and align it with the broader enterprise risk management (ERM) strategy.
The NIST Interagency Report (IR) 8286 Revision 1, released in December 2025, does not attempt to solve that challenge with a new theory. It does, however, address the subject by reinforcing how cybersecurity is expected to function as a cog within the ERM strategy. The updated guidance clarifies how cyber risk information should be contextualized, aggregated, and, when feasible, expressed in quantitative terms so it can be evaluated alongside other enterprise risks.
Throughout the document, the emphasis remains on integration and presenting cyber risk in a form that supports action.
From Cybersecurity Practice to Enterprise Risk Input
The NIST IR revision positions cyber risk squarely within the broader enterprise risk landscape. The framing is both deliberate and explicit, leaving little room for interpretation. “Cybersecurity risk is an important type of risk for any enterprise…[on par with] financial, legal, legislative, operational…and supply chain risks” (pg. 1). Such a positioning removes any implied separation between cyber and other enterprise concerns, ensuring it is treated with the same rigor leadership applies to other objectives.
Responsibility for cyber risk within the enterprise context is also addressed directly in the document’s latest iteration. “Senior leaders…have a unique responsibility to holistically manage the combined set of risks, including cybersecurity risk” (pg. 1). By putting cyber on equal footing with other forms of fiduciary and reporting duties, NIST IR is dispelling any misconceptions that executives need to engage in technical oversight. Rather, it is insinuating that cyber risk information must reach them in a form that supports governance.
Cyber Risk Registers Sit at the Center of Integration
Another component of IR 8286 Rev. 1 that sees sustained emphasis is the cyber risk register, underscoring that it should be the primary mechanism for communicating cybersecurity risk during the ERM process. The register itself is described as a shared artifact, as opposed to an internal security deliverable that is riddled with jargon, and should therefore be populated with terms that facilitate board-level conversation and decision making. "The [cyber] risk register provides a formal communication vehicle for sharing and coordinating cybersecurity risk activities" (pg. 1).
Such an unambiguous framing elevates the purpose of the register, articulating that the tool must serve to translate the technical conditions of the organization's cyber exposure into loss scenarios, financial impacts, and likelihoods that executives can easily evaluate alongside other risks. "Organizations are strongly urged to adopt and integrate cybersecurity risk registers into... [the] methodology they are currently using" (pg. 9). What matters is that cyber risk information is structured so it can move upward without losing meaning.
The Growing Importance of Aggregation and Comparability
One of the most prominent themes in the December 2025 revision concerns how cyber risk information progresses from individual systems to organizational views and, finally, to the enterprise level. NIST emphasizes that this upward trajectory of cyber data is fundamental to effective integration with ERM. "Cybersecurity risk registers consistently capture...risk-related information" and ensure it's delivered to the necessary stakeholders (pg. 11). This progression, however, is not intended to be a simple matter of consolidation.
As the information moves up the chain of command, it must evolve to support holistic evaluation and prioritization. "The context of those registers should be aggregated, normalized, analyzed, and prioritized at higher levels,” allowing for the easy transfer of knowledge from cybersecurity risk management (CSRM) to ERM (p. 10). Without such shared definitions, consistent scales, or comparable structures, cyber risks remain difficult to evaluate alongside the many other material enterprise exposures.
In other words, even if the data is technically visible, an absence of aggregation and normalization renders it unsuitable for making higher-level decisions. The updated NIST document reinforces this expectation through both narrative guidance and visual models that show cyber risk flowing into enterprise risk profiles, consistently establishing that, for cyber risk to participate meaningfully in ERM, it must be expressed in a form that allows comparison across risk types rather than remaining bound to system-level detail.
Quantification as an Essential Part of Making Enterprise Decisions
As cybersecurity leaders work towards aggregation and comparability, expressing cyber risk in quantitative terms emerges as the practical next step, which IR 8286 Rev. 1 details with deliberate care. The guidance noticeably stays away from prescriptive requirements, acknowledging the nuances of quantitative analysis, yet it clearly articulates a partiality for financial quantification when conditions allow for it. "Quantitative methods are preferred, given the wide variety of data available" (pg. 25).
Still, it's important to note that this document ties this preference directly with governance rather than overt technical accuracy. "Organizations are encouraged to quantify risk in financial terms...to support defensible prioritization and treatment decisions" (pg. 32). Financial measurement ensures that cyber risk can be assessed in tandem with other exposures that leadership already evaluates through an economic impact and probability lens. In short, financial quantification bridges the gap between the cybersecurity and executive teams.
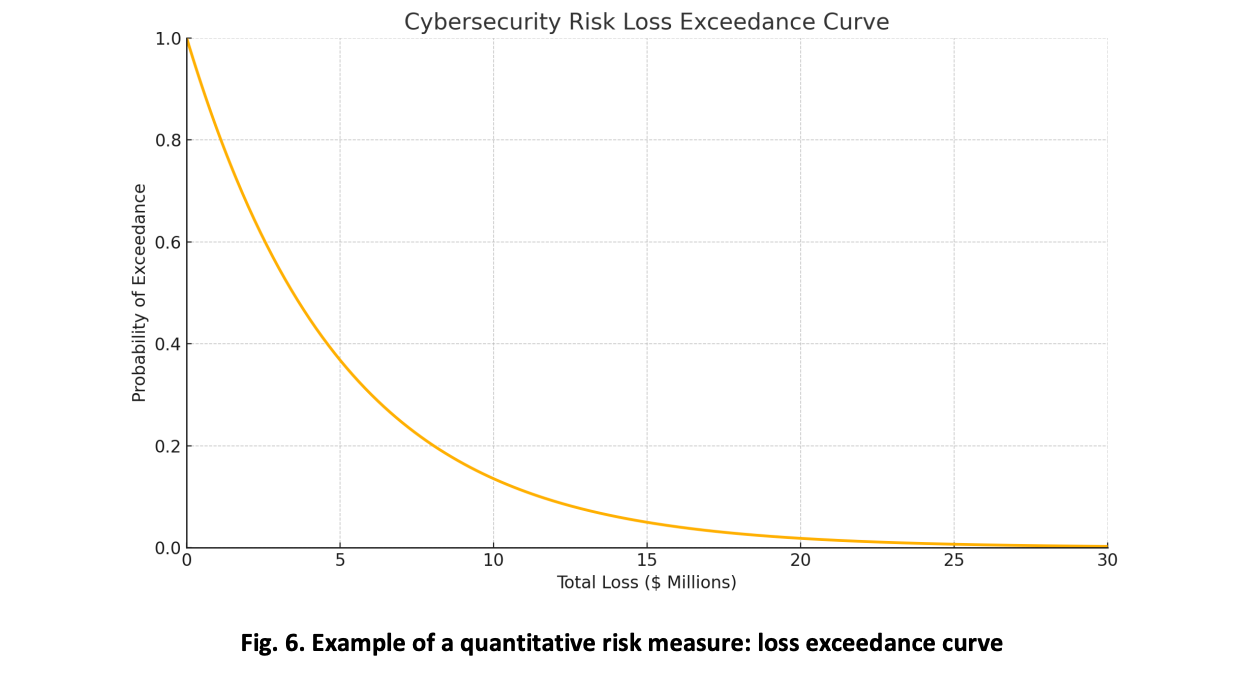
Further stressing the importance of using quantification to integrate CSRM into the broader ERM space, NIST's revision includes a loss exceedance curve (LEC) to more precisely illustrate how results can be presented for enterprise consumption (pg. 29). The chart depicts the probability of losses surpassing defined financial thresholds over a given period. For instance, in the example, the organization faces a 20% annual likelihood of losing roughly $8 million due to a cyber event. Although purely illustrative, the LEC demonstrates how cyber risk can be expressed in a format that supports portfolio-level discussion.
At the same time, IR 8286 Rev. 1 is careful not to position quantitative outputs as sufficient on their own. NIST explicitly acknowledges the limitations of current practices. “Methods such as quantifying cybersecurity risk in dollars and aggregating cybersecurity risks are often ad hoc and are sometimes not performed with the same rigor as methods for quantifying other types of risk within the enterprise” (p. 2). Quantitative results are framed as decision inputs rather than definitive answers, with their usefulness depending on how well they are grounded in business impact analysis, asset importance, and expert judgment.
This balance reflects the pragmatic view of cyber risk management that one needs to make optimized choices. Financial cyber risk quantification (CRQ) supports aggregation and enterprise comparison, while contextual analysis provides the interpretation required for governance decisions. When supported by structured assumptions and calibrated inputs, including historical loss data such as insurance claims, quantified outputs can strengthen the link between cyber risk and the enterprise risk portfolio without displacing judgment.
Business Impact Analysis as an Enterprise Connector
Another area of increased attention in IR 8286 Rev. 1 is the business impact analysis (BIA), serving as the means that connects technical disruptions to organizational consequences. In the past, cyber risk discussions often stopped short at system impact and isolated implications. Now, NIST frames the BIA as the way cyber risk analysis becomes relevant beyond IT environments. "The BIA's purpose is to correlate the system with the critical mission...and characterize the consequences of a disruption" (p. 20).
Impact is also definitively tied to enterprise assets and objectives rather than generic severity ratings. “The relative importance of each enterprise asset will be a necessary input for considering the impact portion of the risk analysis” (p. 20). With this grounding, the BIA provides the context needed to interpret both qualitative assessments and quantitative forecasts. Risk of financial loss, operational disruption, and broader organizational exposure subsequently becomes all the easier to assess.
IR 8286 Rev. 1 repeatedly positions BIA as a key input to prioritization decisions that occur at higher levels of governance. Within this structure, the business impact analysis does not compete with quantitative methods. It informs them. The result is cyber risk information that reflects not only how likely an event may be, but why it matters to the enterprise and where attention should be focused.
A Portfolio Perspective on Cyber Risk
NIST's revision to IR 8286 consistently reinforces the expectation that enterprise leaders engage with cyber risk through a portfolio perspective, rather than as a collection of isolated loss scenarios. "A portfolio view of risk provides insight into all areas of risk exposure, thereby reducing the chances of...facing undesirable outcomes" (pg. 45). Decisions at the executive level are shaped by how multiple risks accumulate and interact, and a portfolio view allows cyber risk to be examined within that same decision context.
That approach, however, relies on discipline in how risk information is structured as it moves upward through the organization. Aggregation enables individual cyber risks to be viewed collectively, while normalization allows them to be evaluated alongside non-cyber risks using comparable frames of reference. Consequently, cyber risk becomes part of a broader enterprise risk picture. Individual scenarios still matter, but their significance is understood in relation to other material exposures the organization faces.
Presenting cyber risk at the portfolio level enables prioritization decisions that reflect overall enterprise exposure. Framed this way, cyber risk can be considered within the same governance and financial contexts that guide other enterprise decisions. “Enterprise leaders will have the necessary information and opportunity to consider cybersecurity exposure as factors for budgets or corporate balance sheet reporting” (p. 41). When packaged as such, choices around resource allocation, trade-offs, and risk acceptance become more straightforward.
Operational Implications for Cyber Risk Programs
The revision also places renewed emphasis on how cyber risk programs function once integration with ERM becomes an operating expectation rather than a conceptual goal. Risk activities must produce outputs that can move beyond technical and IT teams and support governance and prioritization at higher levels of the organization. Cyber risk information is expected to be structured around scenarios, likelihood, impact, response options, ownership, and status in a consistent manner.
Financial expression of cyber risk similarly plays a practical role in this operating model by supporting comparison across risk portfolios. When paired with BIA and expert judgment informed by calibrated inputs such as insurance claims, quantitative outputs provide a common reference point for prioritization discussions. At an operational level, this approach encourages tighter alignment between security, risk, finance, and executive departments. Cyber risk programs become less focused on reporting activity and more focused on supplying decision-ready outputs.
Structuring Cyber Risk for Enterprise Decisions
IR 8286 Rev. 1 reflects a maturation in how cybersecurity is expected to function within the enterprise. The guidance clarifies principles around communication and decision relevance rather than introducing totally new concepts. Cyber risk is treated as an input that must support the same oversight steps applied to other risk management processes. Throughout the updated document, NIST emphasizes consistency in how risk information is shaped as it moves throughout the organization. Scenario-based analysis, aggregation, normalization, and business impact considerations all form the foundation for enterprise-level evaluation.
As such, quantitative expression plays an increasingly important role by enabling comparison across risks competing for executive attention and resources. Programs that produce tangible, business-oriented metrics are better positioned to influence investment and risk acceptance discussions. Financial quantification, specifically, facilitates those conversations by translating cyber exposure into terms that leadership already applies in their management of other enterprise risks.
NIST's IR 8286 Rev. 1 ultimately positions cyber risk management as a critical part of the enterprise decision cycle rather than a parallel activity. When cyber risk is expressed in a form that supports, among other processes, aggregation, comparison, and prioritization, it becomes easier for leadership to evaluate trade-offs and align risk decisions with organizational objectives over time.
To see how cyber risk quantification can support enterprise decision-making and strengthen integration with ERM, explore how Kovrr helps organizations model and manage cyber risk at scale. Schedule a demo.




.webp)