Blog Post
What the Latest Mega Breaches Teach Us About Cybersecurity Board Reporting
August 3, 2025
TL;DR
- The Qantas and Marks & Spencer data breaches sparked industry concern over the lack of governance guiding cyber risk decisions.
- In both cases, it was remarked that executives lacked the context needed to act early and minimize fallout.
- Effective cybersecurity board reporting transforms technical exposure into financial terms, enabling more meaningful executive discussions.
- Mature organizations embed cyber risk into governance practices, align leadership on risk appetite, and maintain oversight even when third parties are involved.
- Cyber risk quantification (CRQ) equips CISOs with decision-useful metrics that strongly motivate board engagement and support proactive investment.
- Without board-level understanding and ownership of cyber risk, security becomes fragmented, and the business remains vulnerable.
When Governance Breaks Down, Breaches Break Through
Both the Marks & Spencer ransomware attack and the Qantas breach dominated headlines for weeks, each exposing serious lapses in how data and risk were managed at the organizational level. But within the cybersecurity community, the response took a different turn. Unlike with other commentary post-cyber incidents, the focus quickly moved away from compromised systems and toward something more structural. These weren’t framed as technical breakdowns. They were described as failures of governance.
In both cases, industry professionals, posting across Reddit threads and LinkedIn feeds, called out the same patterns of weak accountability and a lack of executive visibility into cyber risk. Human error may have served as the initial entry point, and technical controls may have failed to contain the threat. Nevertheless, the broader damage, many argued, was a direct result of the absence of clear ownership and alignment at the leadership level.
Cybersecurity teams cannot operate in isolation from the rest of the business. When strategic decisions around cyber risk are disconnected from the boardroom, prioritization falters, and material risks are left unaddressed. Achieving meaningful outcomes requires mature governance practices and high-level engagement, grounded in consistent data-driven cybersecurity reporting that equips board members with context. Without that foundation, even well-resourced security programs are left exposed.
Structural Blind Spots Amplify Impact
In the aftermath of the Qantas and Marks & Spencer cyber incidents, industry commentary indeed gravitated toward a pattern that had less to do with infrastructure and more to do with internal coordination. While neither company released a full post-incident breakdown, cybersecurity professionals and industry reporters illuminated signs of deeper dysfunction within the organizations, such as slow response times and unclear escalation paths.
Qantas, specifically, faced criticism for how long it took officials to formally acknowledge the breach, as well as for the apparent lack of integration between technical response teams and corporate communication. In the case of Marks & Spencer, observers noted that the attack most likely involved a third-party service provider, which subsequently raised concerns about visibility into outsourced systems and the chain of accountability during incident response plans.
The common thread between these two events, and most likely several others that have occurred in recent years, was that those responsible for managing risk were neither coordinated nor fully informed, allowing the situation to escalate further than it might have with clearer communication and stronger oversight. Had the relevant stakeholders been better equipped with timely, decision-relevant insights, particularly around exposure and business impact, the fallout may have looked very different.
The Strategic Purpose of Cybersecurity Board Reporting
Effective cybersecurity board reporting should not be treated as merely a compliance exercise, nor should it be replete with technical terminology. Its core purpose is to bridge operational cyber realities with strategic oversight and planning, giving board members and other executives the tangible information necessary for them to understand cyber exposure, allowing them to optimally allocate resources and make informed, holistic decisions.
Strong board reporting, therefore, distills cyber risk into formats that reflect the organization's financial and operational posture, including clear articulation of quantified loss scenarios, such as how likely the enterprise is to experience a specific incident, along with the respective impact should it remain unaddressed. It also incorporates modeling how proposed controls or other mitigation investments will reduce exposure levels, making tradeoffs visible and defensible.
When delivered consistently, this type of reporting develops the shared context required for board members to engage in meaningful oversight, helping them to assess whether the current cyber risk posture aligns with the organization's risk appetite and whether mitigation efforts and investments are having a material impact on exposure. Most importantly, it enables leaders to recognize when the status quo is no longer acceptable, ensuring they can intervene early enough to prevent avoidable damage.
Governance Gaps That Cyber Events Keep Exposing
Rarely do post-mortem reviews disclose a novel attack vector. In fact, the technical details often repeat themselves. What does emerge, however, even when details are sparse, is that governance practices were either missing or, in many cases, cybersecurity board reporting was sporadic at best. Cyber risk management insights might have arrived too late, or they were not appropriately escalated, limiting the leadership team's ability to help shape or challenge decisions before they were formalized.
Another issue that routinely emerges is suboptimal communication. When cyber risks aren’t framed in operational or financial terms, it’s difficult for board members to evaluate security programs vis-à-vis other business plans. Priorities are consequently weighed without the full context and a clear view of the trade-offs, and some initiatives advance despite introducing levels of exposure the organization wouldn’t knowingly accept.
Outsourcing, as is common for enterprises, only sharpens the blind spots. Handing over critical operations to third-party service providers abroad might initially be cost-effective, but it inevitably reduces internal control and distances accountability. As one professional remarked, organizations “might think [they’re] paying for ‘expertise,’ but what [they] often get is a minimal service… while [losing] all situational awareness.” Over time, these shortcomings not only weaken cybersecurity. They compromise the governance structures meant to oversee it.
What Mature Cyber Risk Governance Looks Like
First and foremost, organizations with strong cyber governance don't treat cybersecurity as an isolated function. They embed it into high-level decision-making practices, ensuring the CISO, CFO, and CEO are aligned in their understanding of overall exposure and appetite, as well as according to their specific domains. The board plays a leading role in setting these thresholds and, more importantly, takes accountability for evaluating the tradeoffs and finalizing strategies.
In these mature environments, cybersecurity is discussed in the same cadence and language as other forms of enterprise risk. Cyber risk scenarios, likewise, are modeled and quantified to give board members a tangible appreciation of how likely they are to occur and how much they could cost the business. Control implementation prioritization is justified based on the projected impact, and cybersecurity board reports are delivered regularly to evaluate whether the overall posture is improving and why.
Crucially, governance is maintained even when external partners are involved. Third-party service provider risk assessments are invested in with the same amount of rigor as internal ones, and oversight mechanisms remain intact. The result, of course, isn't a risk-free environment. Human behavior, complexity, and uncertainty still introduce variability.
Nevertheless, what matters most is the sustained commitment. The risks that the business invests in understanding, measuring, and managing, however imperfectly, are the ones they’re best equipped to mitigate.
CRQ’s Role in Empowering Better Cybersecurity Board Reporting
The breakdown that typically exists in an enterprise's cyber governance primarily stems from how risk is communicated. Dashboards track technical activity, so CISO reports reflect these operational realities, rather than the business exposure. Cybersecurity board presentations will even include the controls in place, but explain neither what the controls are protecting nor what's at stake if they fail. Ergo, executives are forced into the position of making strategic decisions without a clear understanding of the potential consequences.
Cyber risk quantification (CRQ) instantly repositions these conversations. Instead of measuring metrics like mean time to exposure or phishing email click-through rates, it measures financial exposure, enabling CISOs to deliver cyber risk intelligence in a format that's both accessible and relevant to the board. When it's known, for instance, that there is a 30% likelihood of suffering from an event that will cost $5 million, it becomes much easier to integrate cyber considerations into broader business discussions.
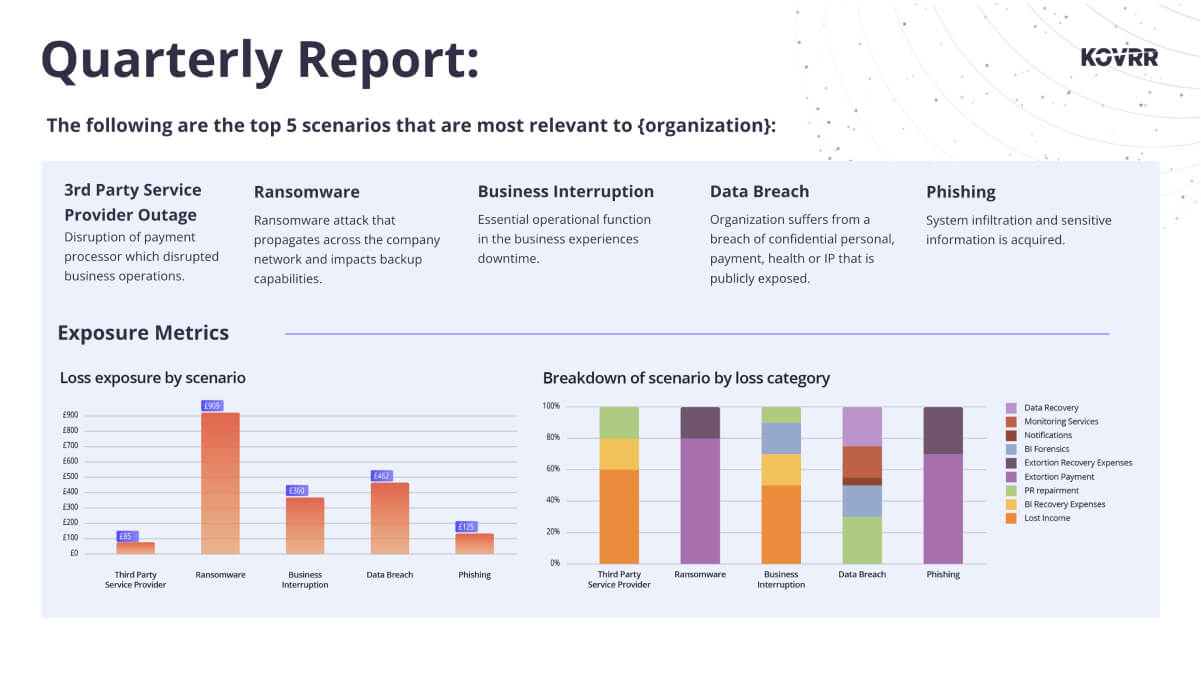
Indeed, with resilience on the line, many leaders are now driving this shift by adopting scenario-based cyber risk modeling, often starting with a forecast of the five most financially significant events the organization may face in the coming year. Because scenarios are presented alongside quantified loss projections, including visual breakdowns of how costs accrue across categories like business interruption, recovery, and extortion, board members quickly grasp the scale and nature of their exposure.

Another common use case for leveraging CRQ in cybersecurity board reporting is to justify budgeting decisions. Armed with financial metrics in place of vague threat landscape forecasts, CISOs can demonstrate how proposed investments not only reduce exposure but can also generate a positive ROI. The monetary framing repositions cybersecurity from a cost center to a strategic enabler, one that facilitates growth rather than simply consuming budget, a perspective that highly motivates the board to allocate the necessary time and resources.
Cybersecurity Isn’t Secure Without Governance
By the time a data breach has reached the headlines, the technical failure or initial attack vector has long since surfaced. What's harder to see, but often far more damaging, is the leadership vacuum that let the event unfold in the first place. In both the Qantas and Marks & Spencer incidents, the deeper concern raised by community members wasn't that something went wrong. Instead, it was that there were apparently no mechanisms in place to ensure the right people knew what was at stake or when to act.
These breaches, among the many others that are occurring daily, are a direct result of when cyber risk reporting is not a consistent practice. When interaction is limited, CISOs may not realize that technical metrics need to be discarded, and boards, in turn, don't learn how to ask the questions that will allow them to make more informed decisions. Boards can't govern what they don't understand, nor can executives intervene. Gaps grow wider, and consequences compound.
Mature governance demands regular CISO engagement, with discussions being conducted in a language that all key stakeholders comprehend. While this maturity doesn't ever guarantee a perfect outcome, it can ensure that cyber risk is acknowledged and debated, not ignored, making the difference between reacting after the impact and mitigating the threat before it hits. Cybersecurity is a leadership responsibility, and if boards aren't governing it, they're not protecting the business.
If your board isn’t getting the context it needs to govern cyber risk effectively, now is the time to rethink how those conversations are structured. Schedule a free demo with one of our experts to learn more.



.webp)
%20Trends%20-%20Blog%20Image%20(1).jpg)
